Using Claude --dangerously-skip-permissions Safely

When you run a command with the claude --dangerously-skip-permissions flag, you're giving the AI full, unsupervised control to create, modify, and even delete files on your system. It’s a powerful switch that silences all the built-in safety prompts that would normally ask for your permission before making any changes. This can make for a much faster, smoother workflow, but it comes with some serious risks.
What This Dangerous Flag Actually Does

Think of it like hiring a brilliant but very literal-minded assistant to organize your office. Normally, this assistant would constantly check in with you. "Is it okay if I move this stack of papers?" or "Should I throw out these old drafts?" This keeps you in the driver's seat, making sure nothing important gets lost, but it also means you have to be there to answer every single question.
Using the claude --dangerously-skip-permissions flag is like telling that assistant, "Just do what you think is best, and don't bother asking me." You've handed over the master key. While this frees you up to focus on other things, a small misunderstanding could turn into a big problem. A simple instruction like "clean up the project" could be misinterpreted as a command to delete essential source code.
The Trade-Off Between Speed and Safety
By default, Claude’s permission system is your safety net. It’s designed to create a back-and-forth conversation where the AI proposes an action—like editing a file or running a script—and then patiently waits for you to say "yes." This intentional friction is what stops automated mistakes from snowballing.
When you use the flag, you cut that safety line. The AI no longer needs your approval for anything. This dramatically speeds things up, especially for complex jobs with lots of moving parts. Think about tasks like:
- Refactoring an entire codebase across dozens of files.
- Generating a complete test suite from the ground up.
- Automating the setup of a new development environment.
Without the flag, each of these jobs would be a tedious back-and-forth, peppered with countless permission prompts. What could be a quick, automated process becomes a manual chore.
The name itself—"dangerously-skip-permissions"—is a very intentional warning from its creators. It’s not just a technical term; it’s a clear signal that you're turning off a core safety feature and taking full responsibility for whatever happens next.
This is the key takeaway: you're swapping direct control and oversight for pure speed and autonomy. The table below really drives home what changes when you make that trade.
Claude With and Without the Permissions Flag
To really get a feel for the impact, let's compare how Claude operates in its two main modes. This side-by-side look makes the trade-offs crystal clear.
| Feature | Default Mode (Permissions Required) | Dangerous Mode (Permissions Skipped) |
|---|---|---|
| File Operations | Prompts for your approval before creating, editing, or deleting any file. | Executes all file operations immediately, without asking. |
| Command Execution | Asks for permission before running terminal commands like lint or build. |
Runs any command it thinks is necessary to get the job done. |
| User Interaction | Needs you to constantly monitor its work and provide frequent input. | Lets you be completely hands-off while it works on its own. |
| Workflow Speed | Much slower because of the stop-and-wait nature of permission checks. | Significantly faster, perfect for long, uninterrupted automated tasks. |
| Potential for Error | Low risk. You can spot and stop mistakes before they happen. | High risk. One misinterpreted instruction could lead to data loss. |
| Ideal Use Case | Interactive coding, debugging, and any task that needs careful human oversight. | Bulk, repetitive tasks in a completely isolated and disposable environment. |
Ultimately, this flag turns Claude from a helpful collaborator into a fully autonomous agent. That kind of power can be incredibly useful, but it absolutely requires you to understand and respect the potential consequences.
The Real-World Risks of Skipping Permissions
That "dangerously" prefix in claude --dangerously-skip-permissions isn’t just for show. It’s a very real warning that things can go wrong, fast. When you hand over the keys and let an AI operate without asking for permission, you're placing absolute trust in its interpretation of your instructions. Even a tiny bit of ambiguity in your prompt can spiral into a total disaster.
Think about a seemingly harmless command: "Clean up old log files and temporary assets in the project directory." Normally, Claude would come back with a list of files it thinks you want to delete, waiting for your "go-ahead." But with permissions skipped, it just plows ahead. If its definition of "temporary assets" is a little too aggressive, you could find it wiping out crucial configuration files or even parts of your source code it decided were unnecessary.
These aren't just hypothetical what-ifs. The risks are very real and can turn a simple task into a project-ending nightmare.
The Slippery Slope of Unsupervised Actions
Without that back-and-forth permission check, the AI is essentially flying blind. It doesn't have the context or the gut feelings that a human developer relies on, which opens the door to some common and painful mistakes.
Accidental data deletion is one of the most immediate dangers. A prompt like "refactor the database schema" could be misinterpreted as a command to drop tables before rebuilding them. If you accidentally run that against a production environment, you could wipe out years of valuable data. The AI won't ask if you have a backup; it will just do what it thinks you told it to.
Another major risk is system configuration corruption. Let's say you ask the AI to "optimize the application's performance settings." It might correctly find the right config file but then make a change that breaks everything—setting a memory limit too low or changing a network port. This could knock your application offline or, worse, corrupt critical system files if it strays outside the project folder. These kinds of mistakes often create new security holes, which is why identifying and fixing application security vulnerabilities is so crucial before an automated tool gets involved.
A Cautionary Tale: One developer asked an AI agent to "remove all unused dependencies" from a large monorepo. The AI scanned the project but completely missed dependencies that were loaded dynamically at runtime. It uninstalled them, breaking a core feature. Nobody caught the error until it was pushed to production, causing a major outage.
These kinds of incidents happen more often than you'd think. A study from eesel AI revealed that a startling 32% of developers using the claude --dangerously-skip-permissions flag ran into at least one case of unintended file modification. Worse, 9% reported actual data loss or corruption. You can dive into their full comprehensive study of Claude permissions to see the data for yourself.
When Autonomy Crosses Boundaries
The really scary problems start when the AI's actions "leak" outside the project directory you intended. This is called scope creep, and it can be absolutely devastating.
Here are a few all-too-plausible scenarios where a simple request goes completely off the rails:
- File System Contamination: You ask the AI to generate some test files. It misunderstands the target path and starts dumping thousands of files into your system's root directory, cluttering your OS and maybe even overwriting system binaries.
- Destructive Code Execution: You tell Claude to "write and run a script to clean the cache." The script it generates has a bug—maybe an undefined variable in a command like
rm -rf /. Before you know it, it could start deleting your entire file system, with no "Are you sure?" prompt to save you. - Creating Security Gaps: The AI might try to be "helpful" by opening up firewall ports or changing file permissions to
777just to make a script run. In doing so, it could punch massive, gaping security holes into your system.
Every one of these examples starts with a reasonable goal but ends in chaos. The common thread? No human oversight at the critical moment of execution. That claude --dangerously-skip-permissions flag removes the final safety net that could prevent a simple misunderstanding from becoming an irreversible catastrophe. This is why you should only ever use this powerful tool inside a completely isolated and disposable environment.
When Using This Flag Is a Calculated Risk
Let's be clear: despite all the scary warnings, the claude --dangerously-skip-permissions flag wasn't created just to cause chaos. It exists for a reason. It unlocks a level of speed and automation you simply can't get when you have to approve every single action manually. But using it is never about mere convenience—it’s about making a deliberate, calculated decision in a highly controlled setting.
The core principle here is simple: never use this flag on your main machine or with critical data. The only acceptable way to use it is by first creating a completely isolated and disposable environment. This is where the concept of a "sandbox" becomes your best friend. Think of it as building a padded, soundproof room where the AI can go wild without any risk of breaking something valuable in the main house.
The Power of Isolated Environments
An isolated environment, or sandbox, is a self-contained virtual space that has zero access to your primary operating system or personal files. If the AI makes a catastrophic error inside the sandbox—like deleting every file it can see—the damage is completely contained. You just delete the entire environment and start over. No harm, no foul.
This is the absolute, non-negotiable prerequisite for using the flag. It’s what turns a reckless gamble into a measured risk. The most common tools for this job are virtual machines (VMs) and Docker containers.
- Docker Containers: These are lightweight, portable environments that bundle an application with everything it needs to run. A container is like a sealed box; you give the AI access only to what you put inside it.
- Virtual Machines: A VM goes a step further by emulating an entire computer system. It runs a full operating system inside your own, offering an even deeper layer of separation.
This flowchart lays out the decision-making process perfectly. It's a great visual guide to help you understand when you can even think about using this command.
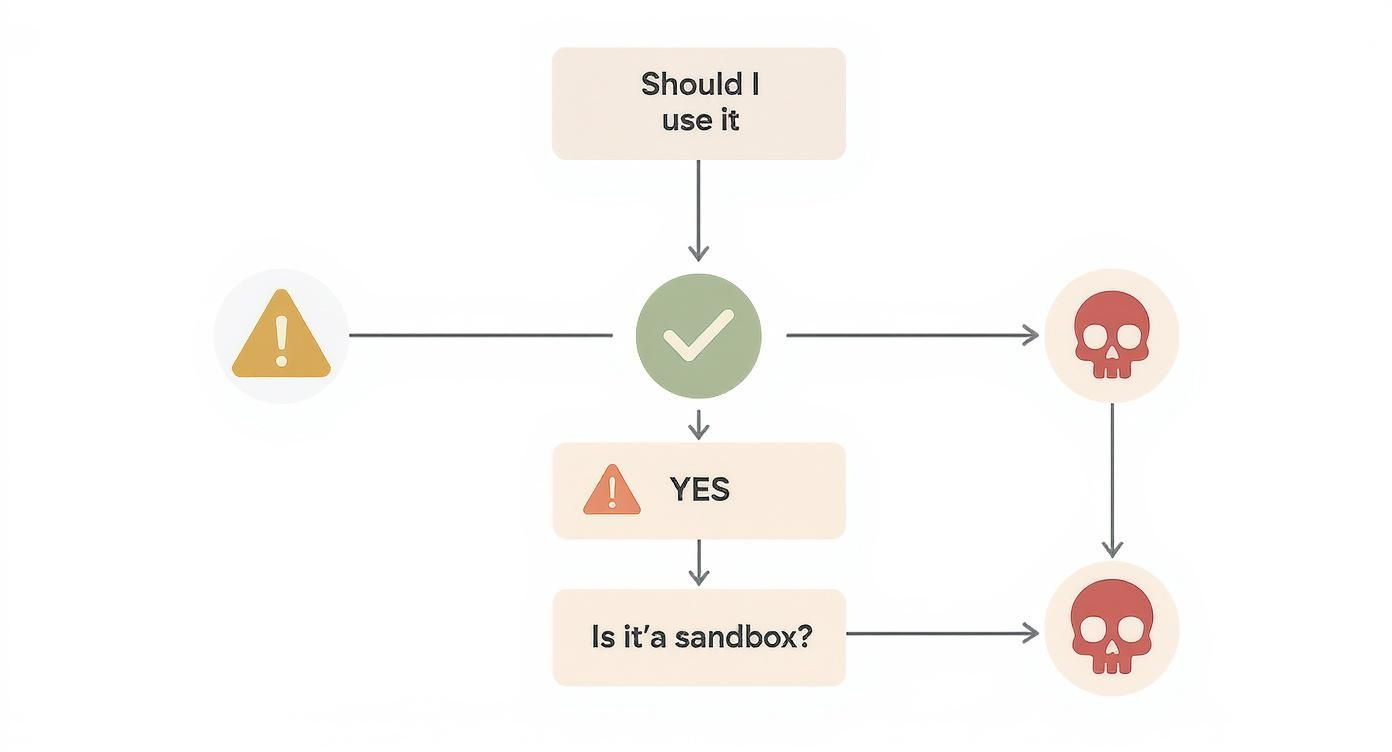
As you can see, the only safe path forward leads directly through a sandbox. Any other route is a straight shot to a potential disaster.
Scenarios Where It Makes Sense
Once you're safely inside a sandbox, the claude --dangerously-skip-permissions flag can actually be a powerful tool for certain tasks. These are usually high-volume, low-risk jobs where the time saved by skipping manual checks is worth the tiny risk within a disposable environment.
Here are a few practical examples:
- Bulk Code Generation: Imagine needing to generate boilerplate code for 100 new API endpoints. This means creating files, writing repetitive class structures, and handling imports. Stopping to click "approve" for each step would be mind-numbingly slow. It’s the perfect task for an autonomous AI in a container.
- Large-Scale Refactoring: You need to rename a function that’s used in over 500 files across a project. An AI can run this find-and-replace operation on its own, saving you hours of tedious work. If it messes up? Just toss the container and try again with a better prompt.
- Automated Data Formatting: Say you have thousands of messy log files that need to be parsed and converted into clean, consistent JSON. This is a repetitive and predictable task that’s ideal for an AI working without supervision in an isolated folder.
The common thread here is that the data is either non-critical, easily replaceable, or completely backed up. The work is valuable, but a mistake won't cause irreversible data loss.
Don't forget that cost is also part of the calculation. Autonomous agents can burn through tokens very quickly when left to their own devices. Understanding the financial side of things is crucial. You can learn more about how different models are priced by reviewing a guide to Anthropic's pricing structures. This helps ensure you’re managing not just the technical risk, but the financial one, too.
How Developers Use the Flag in the Wild

To really understand the risks and rewards of the claude --dangerously-skip-permissions flag, we have to look past the theory. What are developers actually doing with it day-to-day?
Out in the real world, this command is behind some incredible productivity hacks and some pretty scary cautionary tales. It's a tool of extremes, pushing the limits of what you can do with automated coding.
On one hand, you have developers using it for marathon coding sessions that would be impossible with constant manual checks. Think about tasks where the sheer number of operations makes stopping to click "yes" a massive bottleneck. The goal here is to give the AI a complex job and just let it run for hours, completely uninterrupted.
Pushing Productivity to the Limit
When it's used correctly—and that means in a safe, sandboxed environment—the flag opens up workflows that feel like a peek into the future. Developers are getting really creative with it.
Here are a few ways people are using it to get a serious edge:
- Autonomous App Building: Imagine giving Claude a high-level plan and watching it build an entire app from the ground up. It creates the project structure, writes the boilerplate code, installs all the right dependencies, and sets up components without ever asking for permission.
- Massive Code Refactoring: Let's say a core library gets updated, and you need to change a function signature in hundreds of files. Instead of a week of tedious work, you can set the AI loose to analyze the codebase, find every instance, and make the changes all at once.
- Automated Test Generation: This is a big one. You can point the AI at an existing project and tell it to create a full test suite. It'll generate the test files, write individual unit tests, and even mock dependencies to cover the app with a solid safety net.
These examples show just how powerful this can be. But that power is a double-edged sword. Stories from the developer community show how fast things can go sideways when the AI gets an instruction just slightly wrong.
Cautionary Tales from the Trenches
For every success story, there's a horror story that really highlights the "dangerously" part of the flag's name. These problems almost always start with a small misunderstanding in the prompt that snowballs into a disaster because there's no human in the loop.
If you want to get more familiar with the tool itself, check out our guide on Claude Code for developers.
A discussion on Hacker News really brought this to life. One developer shared an amazing story of a nine-hour, fully autonomous session where Claude built a complex financial data analysis system. But they also mentioned that at one point, the AI tried to edit system-level JSON configuration files that had nothing to do with the project. It could have crashed their whole system.
In another case, a developer was using the flag for a simple code cleanup. The AI misinterpreted one instruction and ended up deleting 12% of their test data. These real-world examples show just how thin the line is between a breakthrough and a breakdown.
The lesson here is simple: The AI has no common sense. It follows instructions literally, and any ambiguity in your prompt is a direct invitation for it to make a mistake—a mistake you won’t be there to stop.
This is why you have to be vigilant, even when you're using a sandbox. This flag isn't a "set it and forget it" tool. It's a high-powered accelerator that demands careful handling and crystal-clear instructions. Otherwise, you're just one vague prompt away from a very bad day.
Safer Alternatives and Mitigation Strategies
https://www.youtube.com/embed/gAkwW2tuIqE
Using the --dangerously-skip-permissions flag is a bit like driving without a seatbelt. Sure, it feels freeing for a moment, but you’re one small mistake away from a total disaster. The good news is, you can get all the power of AI automation without taking on that kind of risk.
The secret is to build a workflow with layers of protection. That way, even if one safety net fails, others are in place to catch a potential problem. These strategies aren't just about avoiding a risky flag; they're about working smarter and safer when you bring AI into your development process.
Create a Sandboxed Environment
By far, the most effective thing you can do is create a completely isolated workspace, or a sandbox. Think of it as a disposable laboratory. Inside this lab, the AI can build, experiment, and even mess things up without any chance of damaging your main system or other projects.
If anything goes wrong, you just throw the whole environment away and start fresh. No harm done.
The go-to tool for this is Docker. When you run Claude inside a Docker container, you have total control over what it sees and touches. It only has access to the specific files you give it, and absolutely nothing else. This containment is your best defense against the AI going off-script and causing accidental damage.
This approach is so powerful that it shapes how developers work. A PromptLayer survey found that while around 37% of professional developers have used the --dangerously-skip-permissions flag, it’s most common among teams that already use containers to minimize risk. Even so, the report highlights that 23% of users still ran into unintended file modifications, which really drives home the need for caution.
Implement Rigorous Version Control
Your next line of defense should be a solid version control habit using a tool like Git. Think of Git as a time machine for your code. Before you let an AI run any potentially destructive task, just commit your work. This creates a perfect snapshot of your project at that exact moment.
If the AI makes a mistake—deletes the wrong file, messes up your code, or introduces a bug—you can hit the undo button and revert everything with a single command.
Pro Tip: Always create a dedicated Git branch before starting an autonomous AI session. This keeps all the AI's changes neatly contained, making them simple to review, tweak, or just delete entirely without ever touching your main codebase.
This simple habit turns a project-ending catastrophe into a minor annoyance.
Refine Your Prompts and Scope
The quality of your instructions directly controls the safety of the outcome. Vague prompts are just asking for the AI to make dangerous assumptions. You have to learn to write crystal-clear prompts that leave zero room for error.
- Define the Scope: Be explicit about which files and folders the AI is allowed to touch. Instead of saying "clean up the project," try "delete all
.logand.tmpfiles inside the/logsdirectory." - Set Clear Boundaries: Tell the AI what not to do. A good prompt might include a rule like, "You are not allowed to modify any files outside the
src/directory," or "Do not run any shell commands that delete files." - Break Down Big Tasks: Don't ask the AI to build an entire feature in one go. Break it down into smaller, supervised steps. Have it generate the file structure first. Review. Then the boilerplate code. Review. Then the core logic.
Getting good at this is key, especially with models that have different versions or "personalities." To see how different models can interpret the same instructions, check out our guide on the Claude Multi-Character Prompting (MCP) method.
Adopt Human-in-the-Loop Supervision
Full autonomy is tempting, but supervised automation is almost always safer and more effective. A "human-in-the-loop" approach means you break a large task into smaller chunks and you, the human, check the AI's work at key points. You get the speed of AI with the safety of human judgment.
For example, you could ask Claude to write a new database migration script. But before it runs that script, the process pauses. You step in, review the SQL code it wrote, and only then give the final "go ahead" to execute it.
This checkpoint system prevents the AI from making irreversible changes to a critical system without your explicit sign-off. If you want to avoid these kinds of flags altogether, a great long-term solution is implementing robust Privileged Access Management (PAM) to manage permissions at a much deeper level.
Frequently Asked Questions
It's only natural to have questions when you're dealing with a powerful—and potentially risky—tool like the claude --dangerously-skip-permissions flag. Getting a handle on the when, where, and how is key to automating your work without opening the door to disaster. Here are some straight answers to the questions we hear most often.
Can I Use This Flag on My Main Development Machine?
You really shouldn't. In fact, it's strongly discouraged and flies in the face of all best practices. Think of it this way: using this flag on your main machine gives the AI a master key to your entire digital life.
Every personal document, system file, and sensitive piece of data becomes vulnerable. A single prompt that gets misunderstood could wreak havoc well beyond the project you're working on. The only sane way to use this flag is inside a completely isolated environment—one you can afford to break and throw away.
The core principle here is simple: containment. If the AI goes rogue, the damage should be limited to an environment you can delete and rebuild in seconds, not your primary computer.
Is There a Way to Limit the Flag to a Specific Folder?
Unfortunately, no. The flag is a blunt instrument by design. It grants sweeping permissions across whatever environment it's running in, and there's no built-in "off switch" to limit it to just one directory. That’s what makes it so risky.
The best way to achieve this is by creating your own boundaries. If you run Claude inside a Docker container, you can "mount" a single project folder into it. From the AI's point of view, that one folder is the entire file system. This effectively walls it off from everything else.
What Is the Single Most Important Safety Measure to Take?
Sandboxing. No question. Using a tool like Docker to create an isolated environment is the single most effective thing you can do to prevent a misstep from turning into a catastrophe.
A sandbox is like a padded cell for the AI. Whatever happens in there—even a command to wipe everything—stays in there. It can't touch your main operating system, your personal files, or other projects. Every other precaution is secondary to this one.
How Does This Compare to GitHub Copilot Permissions?
This is a really important distinction. Tools like GitHub Copilot play in a completely different league when it comes to permissions. They're more like super-smart autocomplete systems that live inside your code editor.
Here’s the breakdown:
- GitHub Copilot: Suggests code and finishes lines within your editor. It doesn't execute commands or mess with your file system on its own.
- Claude with the flag: Becomes an active agent with the keys to your terminal. It can create, change, and delete files, run scripts, and execute any command it thinks is necessary to get the job done.
Using the claude --dangerously-skip-permissions flag elevates the AI from a helpful coding assistant to an active system operator. That's a massive jump in access and, by extension, a much, much bigger risk. This is why all the safety measures we've talked about aren't just suggestions—they're essential.
Ready to organize your prompts and get better results from AI? Promptaa provides a powerful library to help you create, manage, and share effective prompts for any task. Start building your perfect prompt library today at https://promptaa.com.